A researcher on Tuesday that they benefit by all web browsers and a trust to be aggressive, protected by the HTTPS protocol, including a website allowed to act as a certification authority rogue CA certificate, to make it acceptable upset verify .
Internet Public Key transportation PKI for digital certificates for Web sites used in the naming of risk. This defenselessness allows MD5 cryptographic hash function MD5 hash is present in the same structure with different messages - an MD5 "as the clash is known, according to the document.
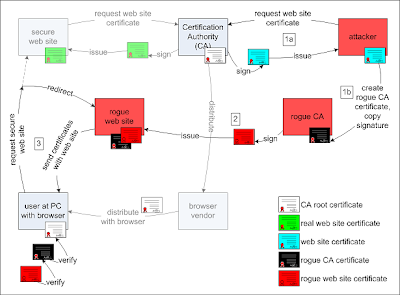
In other words, criminals who are sure in your browser to falsify a CA certificate, so that - certain - a security device on the corner of the page represented by SSL displayed on a Web site to sanction. In particular, the attacker in a transparent man performance against SSL connection - in heart attack and is able to monitor the sites or secure e-mail servers or disrupting traffic.
The system to carry on using MD5 suggested for transition to more safe cryptographic mess functions such as SHA-1 or more preferably SHA-2. Applebee and Sotirov said that the establishment concerned have been notified and were switched to the SHA-1 hash function "very, very soon."
Microsoft, maker of the well-liked Internet Explorer, said the system asked the researchers to take advice "This new exposure does not considerably increase the risk to customers, and that the examiner has not published cryptography backdrop for the attack, and the attack is not repeatable, with no this in order, according to a security optional Tuesday to the software massive." Microsoft is not aware of any active attacks that the problem and actively working with certification authorities to ensure that they are aware of this new research and encourage them to migrate to the new SHA-1 algorithm for signature.
N other words, browsers by criminals who supported on a phony CA credential, so that - that - in a corner of the page represented by blockage in the form of SSL on any web page to display in a point to give permission. In particular, translucent attackers to carry man to SSL - central point attack will be able to monitor and secure servers or websites or e-mail to disturb traffic.
"Proof of success - the notion that the certificate verification of the browsers can be subverted and malicious attackers to control or data sent to websites with insurance may be able to intervene," Sotirov on the project, wrote in a blog post.

No comments:
Post a Comment